Outlook displays the global address list that meets the following criteria:
•The user has permissions to access this global address list.
•The user is a member of this global address list.
•This global address list is the largest of all of the other global address lists.
If you create more than one global address list, and if you want a user to use a specific global address list, make sure that the user is a member of the list, and make sure that the user has permissions to access only this list. You can create custom global address lists and add members to these global address lists.
===========
You can only create Global Address List from Exchange Management Shell.
New-GlobalAddressList -Name 'Shaw' -IncludedRecipients 'AllRecipients' -ConditionalCompany 'shaw'
New-GlobalAddressList -Name 'Telus' -IncludedRecipients 'AllRecipients' -ConditionalCompany 'Telus'
New-GlobalAddressList -Name 'TLC' -IncludedRecipients 'AllRecipients' -ConditionalCompany 'TLC'
Don't modify Default Global Address ListMailbox users whose company attribute is Telus will automatically use the global address list: Telus.
Mailbox users whose company attribute is Shaw will automatically use the global address list: Shaw.
Mailbox users whose company attribute is TLC will automatically use the global address list: TLC.
Create the following mailboxes:
kaiming Liao
Rob Prince
Lina Zheng
Jane Liao
Jonathan Gao
Seungbum Yoo
Kevin Smith
Shane Brown
George Allistair
Alan King
Steve Paulie
Paul Bellitown
Scott Berger
Sarah Carl
$password=read-host "Enter password please!" –asSecureString
$firstName="George"
$lastName="Allistair"
$city="Vancouver"
$company="Telus"
$province="BC"
$department="Network"
New-Mailbox -Name "$firstName $lastName" -Alias "$firstName.$lastName" -OrganizationalUnit 'Terrace.com/Research' -UserPrincipalName "$firstName.$lastName@Terrace.com" -SamAccountName "$firstName.$lastName" -FirstName $firstName -Initials '' -LastName $lastName -Password $password -Database 'USA\First Storage Group\Mailbox Database'
The following mailboxes are from TLC company.
kaiming Liao
Rob Prince
Lina Zheng
Jane Liao
Seungbum Yoo
The following mailboxes are from Telus company.
Jonathan Gao
Kevin Smith
Shane Brown
George Allistair
The following mailboxes are from Shaw company.
Alan King
Steve Paulie
Paul Bellitown
Scott Berger
Sarah Carl
===
create some mail contacts:
$firstName='Catherine'
$lastName='Alcee'
$externalMail='Catherine.Alcee@cdimail.ca'
$OU='Terrace.com/test'
New-MailContact -ExternalEmailAddress $externalMail -Alias "$firstName.$lastName" -Name "$firstName $lastName" -OrganizationalUnit $OU -FirstName $firstName -LastName $lastName
Catherine Alcee belongs to TLC company.
$firstName='Cindy'
$lastName='Pepin'
$externalMail='Cindy.Pepin@cdimail.ca'
$OU='Terrace.com/test'
New-MailContact -ExternalEmailAddress $externalMail -Alias "$firstName.$lastName" -Name "$firstName $lastName" -OrganizationalUnit $OU -FirstName $firstName -LastName $lastName
Cindy Pepin belongs to Telus company.
==
Create some mail user objects:
$firstName='Leesa'
$lastName='Watt'
$externalMail='Leesa.Watt@cdimail.ca'
$UPN='Leesa.Watt@Terrace.com'
$OU='Terrace.com/test'
$password=read-host "Enter password please!" -asSecureString
New-MailUser -ExternalEmailAddress $externalMail -Alias "$firstName.$lastName" -Name "$firstName $lastName" -UserPrincipalName $UPN -OrganizationalUnit $OU -FirstName $firstName -LastName $lastName -Password $password
Leesa.Watt belongs to Shaw company.
$firstName='Tino'
$lastName='Vaswani'
$externalMail='Tino.Vaswani@cdimail.ca'
$UPN='Tino.Vaswani@Terrace.com'
$OU='Terrace.com/test'
$password=Read-Host "Enter password:"
New-MailUser -ExternalEmailAddress $externalMail -Alias "$firstName.$lastName" -Name "$firstName $lastName" -UserPrincipalName $UPN -OrganizationalUnit $OU -FirstName $firstName -LastName $lastName -Password $password
Tino.Vaswani belongs to Telus company.
=====
Get-GlobalAddressList Telus Format-List
IsDefaultGlobalAddressList : False
RecipientFilter : (Company -eq 'Telus' -and Alias -ne $null)
LdapRecipientFilter : (&(company=Telus)(mailNickname=*))
LastUpdatedRecipientFilter : (Company -eq 'Telus' -and Alias -ne $null)
RecipientFilterApplied : True
IncludedRecipients : AllRecipients
ConditionalDepartment : {}
ConditionalCompany : {Telus}
ConditionalStateOrProvince : {}
Update-GlobalAddressList Telus
$global=get-globalAddresslist Telus
Get-Recipient -RecipientPreviewFilter $global.RecipientFilter
Jonathan Gao UserMailbox
Kevin Smith UserMailbox
Shane Brown UserMailbox
George Allistair UserMailbox
Cindy Pepin MailContact
Tino Vaswani MailUser
Get-GlobalAddressList Shaw Format-List
IsDefaultGlobalAddressList : False
RecipientFilter : (Company -eq 'shaw' -and Alias -ne $null)
LdapRecipientFilter : (&(company=shaw)(mailNickname=*))
LastUpdatedRecipientFilter : (Company -eq 'shaw' -and Alias -ne $null)
RecipientFilterApplied : True
IncludedRecipients : AllRecipients
ConditionalDepartment : {}
ConditionalCompany : {shaw}
ConditionalStateOrProvince : {}
Update-GlobalAddressList Shaw
global=Get-GlobalAddressList Shaw
Get-Recipient -RecipientPreviewFilter $global.RecipientFilter
Alan King UserMailbox
Steve Paulie UserMailbox
Paul Bellitown UserMailbox
Scott Berger UserMailbox
sarah Carl UserMailbox
Leesa Watt MailUser
Don't modify the
default global address list
In Active Directory Users and Computers, three global groups: ShawGroup, TelusGroup, and TLCGroup are created.
ADSIEDIT.msc utility


Because default Global Address List includes every mail object, we must deny the member from specific groups to access the Default Global Address List. The member of TelusGroup should access only Telus global Address list; whereas the member of ShawGroup should access the Shaw global Address list.
When a new user is created with a mailbox, please don't assign it to the specific group. After you setup the Outlook client, you assign the user to the specific group.
When you set up outlook clients, they must use the default global address list. If the user don't have permissions or is not a member of the default global address list, the outlook client cannot be set up.
After I deny all the three groups: TelusGroup, ShawGroup, TLCGroup, the new outlook 2003 client cannot be set up. After I allow ShawGroup to access the Default Global Address List, the outlook 2003 can be configured with new mailbox user. With outlook client configured, I deny the ShawGroup to access Default Global Address List.
With Outlook 2007, I didn't experience the odd problem.
Advice: use Outlook 2007 if you implement the multiple GALs.
The above deny permission method has a drawback. It makes the Default Global Address List disappears. New mailbox user cannot be set up in OUTLOOK.
====
How about address lists: ALL USERS, ALL CONTACTS,...?
Since I don't want them, there are several options.
First,
ADSIEDIT.MSC utility, locate the ALL ADRESS LISTS --Properties--Security Tab
AUTHENTICATED Users --Deny List Folder Content
Second,
From Exchange Management Console, I simply remove ALL Users, ALL Contacts, etc.
Third (irrecoverable),
Delete the ALL Address Lists from ADSIEDIT.MSC console. Outlook does not show ALL ADDRESS LISTS. I like that.
===
Whatever you do, if you access your mailbox by OWA, it can see all the address lists. It was solved. Searching for the blog.

 Then, you logon NIFCS\twoodworth from her workstation and logoff her. Her local profile will be uploaded to the server.
Then, you logon NIFCS\twoodworth from her workstation and logoff her. Her local profile will be uploaded to the server.
 Step 3:
Step 3: ====
====


 Step 2:
Step 2:


 VPN Client Access
VPN Client Access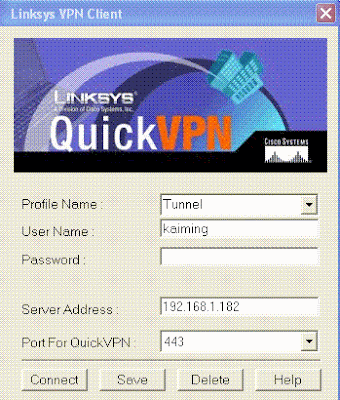 Click Connect button,
Click Connect button,




 ========
======== RV042 at Terrace side:
RV042 at Terrace side:


 For the IPSec configuration, I use the preshared password. All other settings are left alone.
For the IPSec configuration, I use the preshared password. All other settings are left alone. The ping button is quite handy.
The ping button is quite handy. =========
========= VPN Gateway to Gateway:
VPN Gateway to Gateway:

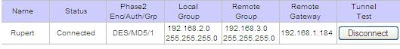 Rupert Router: VPN tunnel:
Rupert Router: VPN tunnel: 


 This domain is VAN.COM, this is you are working on.
This domain is VAN.COM, this is you are working on.


 Display Name of the user object (mailbox) will show in Exchange Management Console. You could set two or more mailboxes with same Display Name.
Display Name of the user object (mailbox) will show in Exchange Management Console. You could set two or more mailboxes with same Display Name.

 The two Canon multifunction copier/printers will be installed in Windows 2003 64bit server. All XP Professional 32bit workstations will automatically install the printer drivers when connecting the printers.
The two Canon multifunction copier/printers will be installed in Windows 2003 64bit server. All XP Professional 32bit workstations will automatically install the printer drivers when connecting the printers.

 User1 Folder's properties:
User1 Folder's properties:
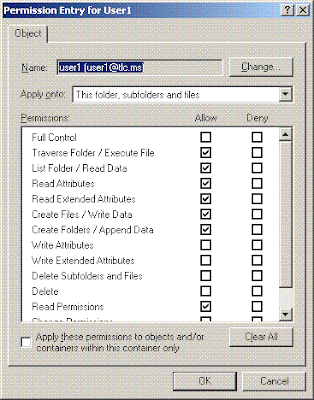 When user1 logs on, he can put files inside the companyFile/User1 folder. But he cannot delete and modify them.
When user1 logs on, he can put files inside the companyFile/User1 folder. But he cannot delete and modify them.